Search Engine for the Internet of Everything
Shodan is the world's first search engine for Internet-connected devices. Discover how Internet intelligence can help you make better decisions.
Sign Up Now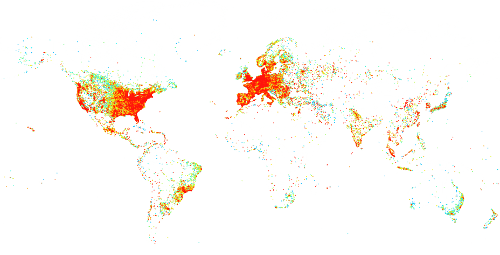
Websites are just one part of the Internet. Use Shodan to discover everything from power plants, mobile phones, refrigerators and Minecraft servers.
Keep track of all your devices that are directly accessible from the Internet. Shodan provides a comprehensive view of all exposed services to help you stay secure.
Learn more about who is using various products and how they're changing over time. Shodan gives you a data-driven view of the technology that powers the Internet.
Within 5 minutes of using Shodan Monitor you will see what you currently have connected to the Internet within your network range and be setup with real-time notifications when something unexpected shows up.
Learn more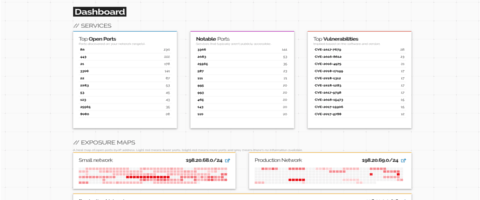

The entire Shodan platform (crawling, IP lookups, searching, data streaming) is available to developers. Use our API to understand whether users are connecting from a VPN, whether the website you're visiting has been compromised and more.
Learn moreShodan crawls the entire Internet every week to give you a truly global perspective.
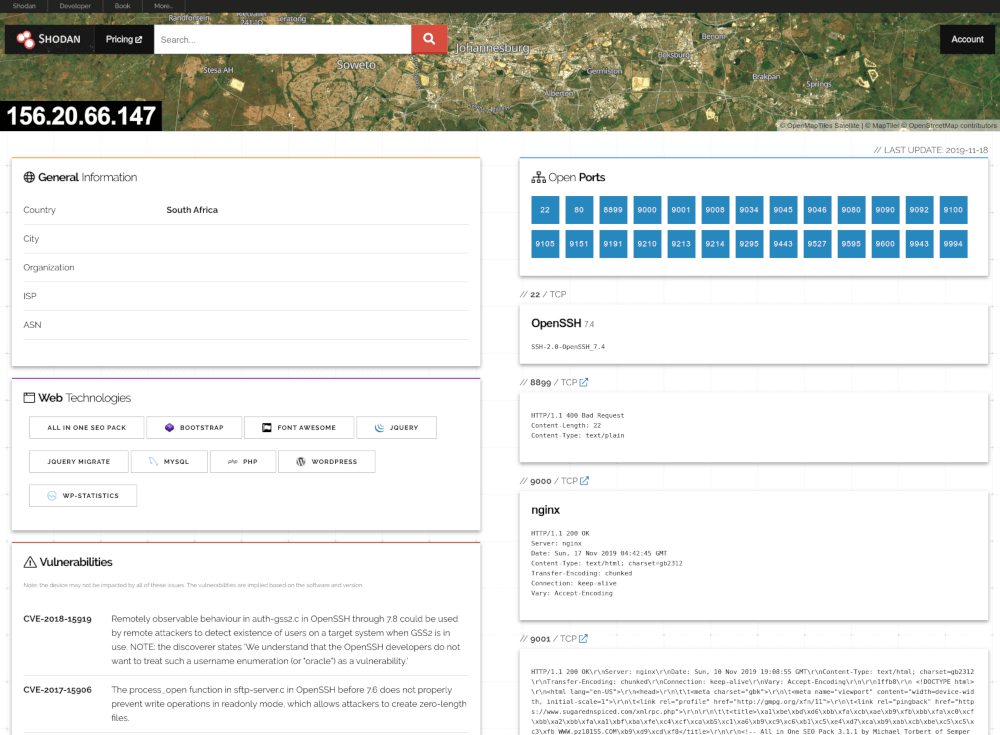
Get a quick view of a website's security by using the browser plugins for Shodan:
Chrome Plugin Firefox PluginCheck out the Shodan Help Center which answers the most frequently-asked questions and provides hands-on guides for common tasks:
Visit Help Center Email Support